This newly founded virus tycoon ransomware has been designed with such an advanced algorithm, so by using those uncommon deployment techniques it can be stay hidden over compromised networks. This malware has been identified an explained by the researchers at BlackBerry who were working with security analysts in KPMG.
This New Tycoon Ransomware Attacking Windows PC
It is a phenomenal kind of ransomware that is written in JAVA, which can be deployed into your system through Java Runtime Environment (JRE) and it is compiled in a Java image called Jimage to hide the malicious purpose. Also read: Do Not Update to Windows 10 May Update!
How it attacks?
To achieve endurance on the victim’s machine, the attackers had used a method called Image File Execution Options (IFEO) injection. Windows registry stores the IFEO settings. Through these settings, developers have a choice to debug the software through the attachment of a debugging application during the execution of a target application.Then a backdoor has been executed with the Microsoft Windows On-Screen Keyboard.After these attackers change the password of the Active Directory servers by disabling the organization’s anti-malware solution through Process Hacker utility.This leaves the sufferer helpless and they are unable to access their own system.Most of the cyber attackers’ files were timestamped including the Java Libraries and the execution scripts, all those files have the same timestamp of 11 April 2020 at 15:16:22. Eventually, attackers successfully executed the latest Java tycoon ransomware module and encrypt all the server files and modules including all the backup system which was associated with the network.
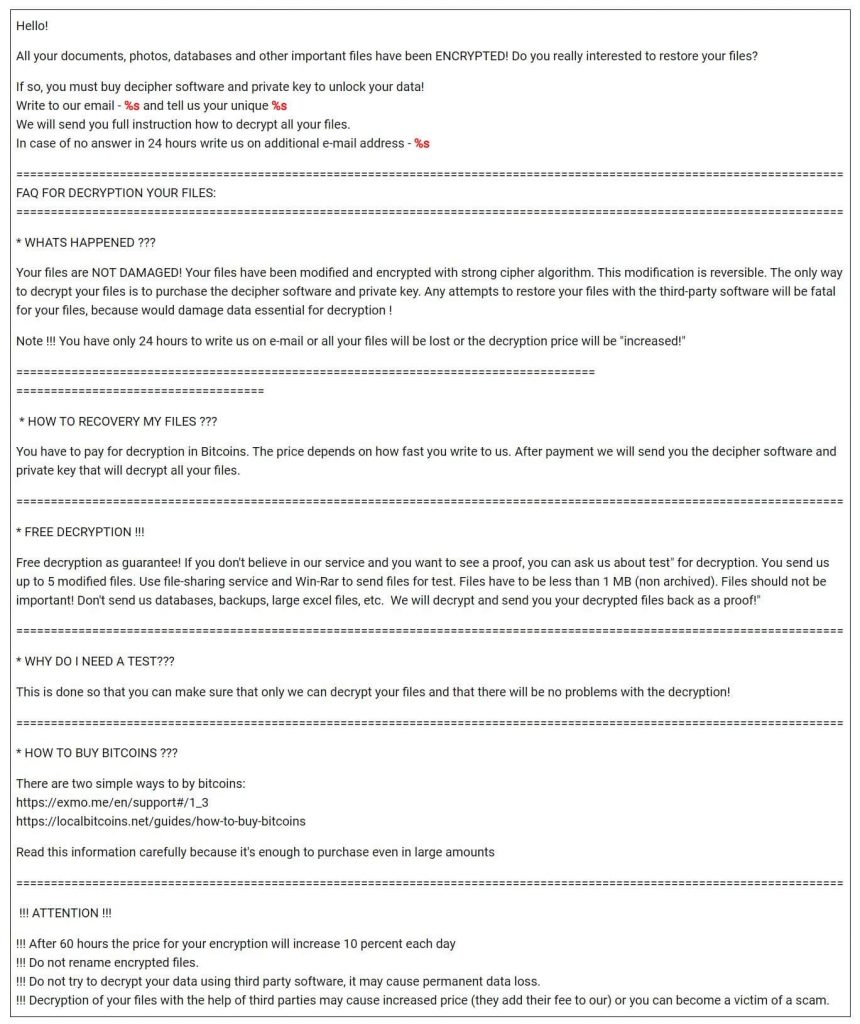
After this malware is installed into your system, i.e. when the zip file gets extracted which is associated with the ransomware, then there are three modules named “tycoon”. That’s why Blackberry named the malware as Tycoon Ransomware. Also read: Do We Need Antivirus in Our Daily Use? Here is a note from the newborn but so dangerous Tycoon Ransomware:
Wrapping Up
To prevent user’s system from such malware organizations should ensure that they are using strong passwords and also make sure that the accounts which need these ports should not have default credentials. Moreover, immediately applying all the updated and available security patches can also reduce the risk as doing this will employ attackers into vulnerabilities. Also Read: Why Anti-Malware Over Antivirus or Vice-Versa?