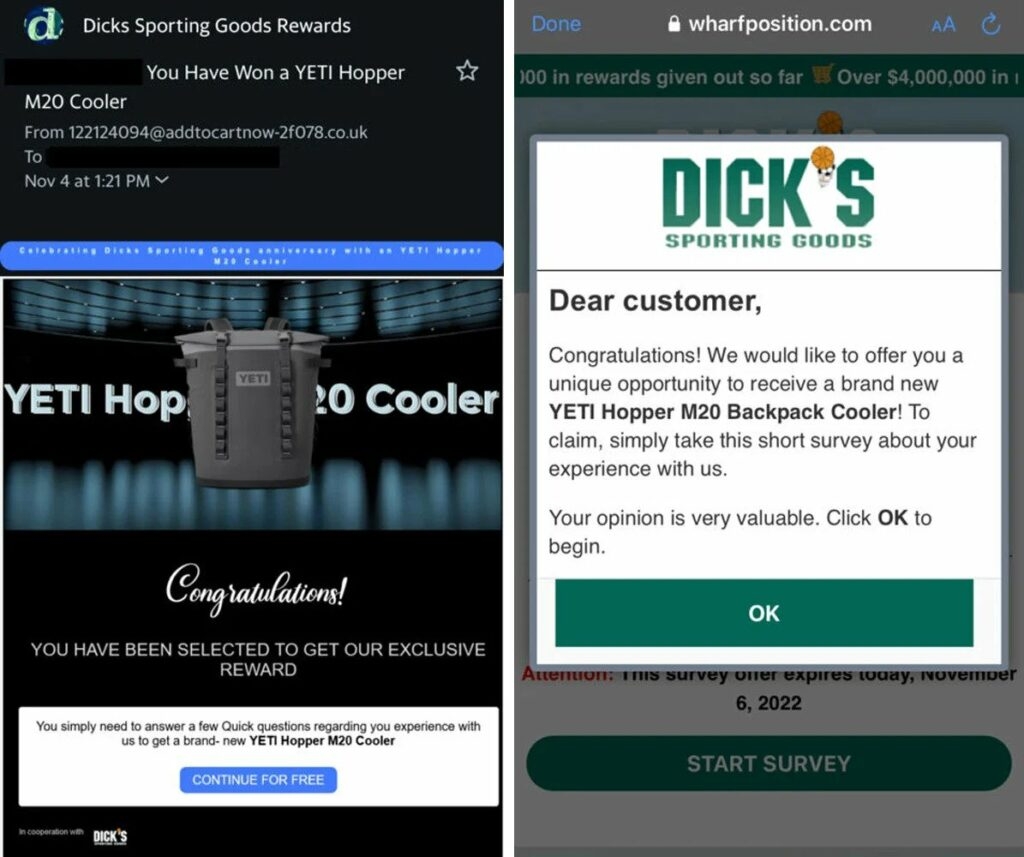
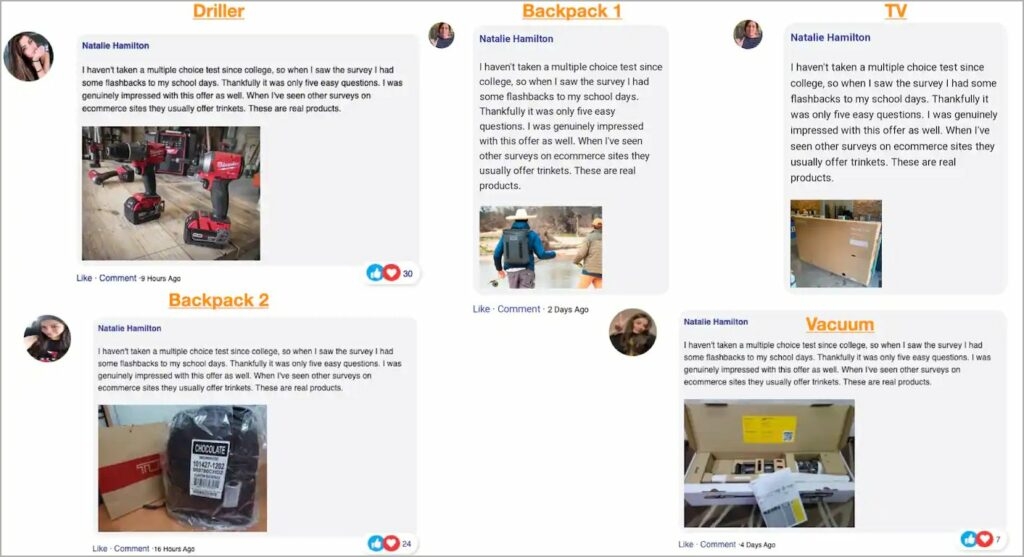
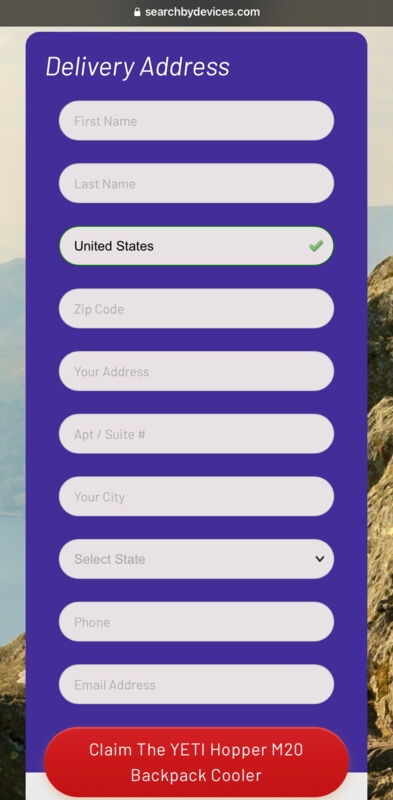
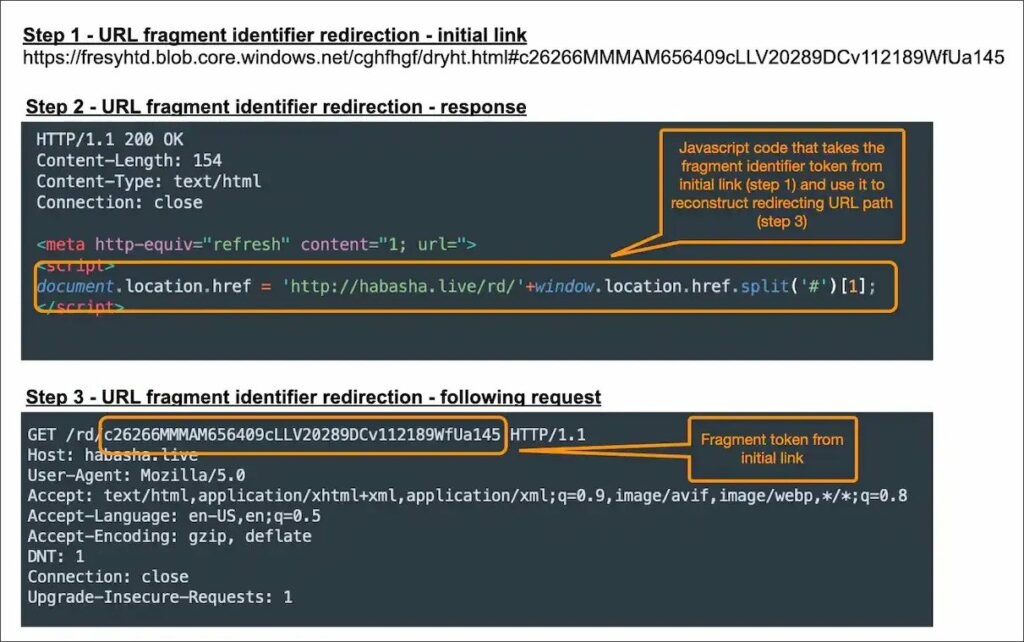
According to Akamai analysts, The attacks have been running since mid-September, focused on Halloween & labor day, and have continued all of October. Also, the phishing kit uses bypassing approach & uses systems to avoid non-targets away from its phishing pages. What is more interesting is that the kit uses a token-based system that makes sure that each target is re-directed to a new phishing page URL. To add to this, the basic idea around these phishing e-mails to potential victims is the chance to win a gift from a trusted brand. The links in the phishing email don’t give any warning signs as they take to the phishing websites several redirections, and at the same time, URL shorteners hide most URLs. Moreover, everyone visiting the phishing website wins the promised price after finishing a short survey and also the five-minute timer, which makes sure that those taking the short survey are filled with a feeling of urgency. Read: Mirai RapperBot Malware Attacking Online Game Servers with DDoS Some of the brands that the attackers imitate include Delta airlines, Sports goods company Dick’s, Tumi (which makes Baggage), and wholesale clubs Costo and Sam’s club. To make the phishing attack more successful, the attackers used fake people reviews showing off the received prizes. To make the phishing attack more successful, the attackers used fake people reviews showing off the received prizes. Well, after winning the prize the victims are then requested to pay for the shipping, and for that, they need to fill in their card details naturally, there are no prizes to be shipped, but rather the payment card details are stolen by the malicious actors. As per the security firm Akamai, approximately 89% of users visiting these phishing domains are from the United States & Canada. Also, based on the user’s location, the phishing domain takes them to a different phishing website which imitates the local brand available there. Each of the phishing emails carries a different link to a landing page with an anchor; for those who don’t know, an anchor is a link that redirects the user to a specific part of a linked-to page. However, in this phishing attack, the anchor tag constitutes a token that is used by JavaScript on the phishing landing page to rebuild the URL to which the target will be redirected. Read: Russia with Love Hacktivists Attacks Ukraine Organizations with Somnia Ransomware Akamai mentions that the values after the HTML anchor will not be considered the HTTP parameters and will not be sent to the servers, yet this value is still accessible by JavaScript code running on the victim’s browser. As for the situation of the Phishing scam, the values placed after the HTML anchor might be disregarded or missed by the security systems that are verifying whether these are malicious or not. Similarly, the value will also be missed by the traffic inspection tool. Inspection tools & Security systems miss this token, so this does not create any risks for the attacker; instead, it helps to keep away researchers, analysts, unwanted traffic, and random people from the phishing landing page. So apart from excluding non-targets, the tokens can be used to track victims, attack performance, etc. Therefore, using all the known methods and avoiding detection makes it a powerful threat to North Americans & Canadians! Read: Qualcomm Announces Snapdragon 8 Gen 2 Flagship SoC